
Hello, I'm Vidhathri
The person who is passionate about learning new technologies.

The person who is passionate about learning new technologies.
I am a student at Amrita Viswa Vidyapeetham. I am currently pursuing B.Tech in Computer Science and Engineering. I am passionate about learning new technologies. I learnt Python, Java, Java Script, HTML&CSS, SQL, PHP. I have some basic knowledge about network security.
I have created this website using Flask and MySQL database. In this website the user can login, logout, delete their own account, the website also has the admin role functionality where the admin can view the details of all the other users. The users of this website can save their blogs and check it whenever they visit the website and all other users of the website can see the blogs of that person.You can access the code of this website from here.
I made this website using PHP and MySQL database. SQL injection is a security flaw that allows attackers to manipulate web applications' database queries by inserting malicious SQL code.This form of cyberattack has been a persistent and evolving menace for decades, making it one of the most critical vulnerabilities in web applications.You can access the code of this website from here.
I made this website using Flask Framework and MySQL database. Cross-site scripting (XSS) is a client-side code injection attack that tricks a web browser into running malicious code. This form of cyberattack has been a persistent and evolving menace for decades, making it one of the most critical vulnerabilities in web applications.You can access the code of this website from here.
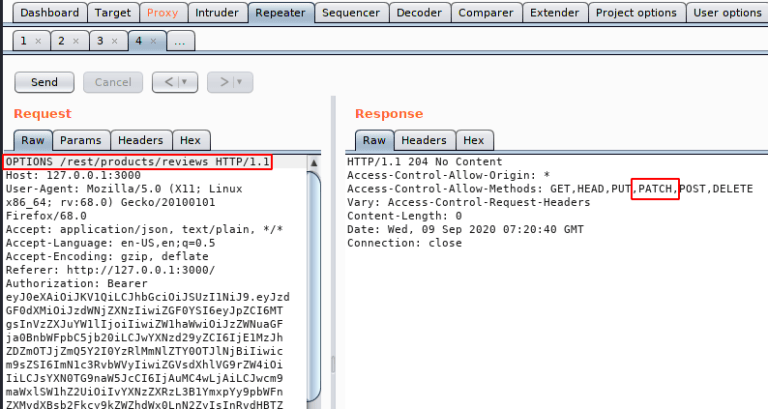
I made this website using Flask Framework and MySQL database. IDOR stands for insecure direct object references, a type of vulnerability that arises when user-supplied input is used to access objects directly. This form of cyberattack has been a persistent and evolving menace for decades, making it one of the most critical vulnerabilities in web applications.You can access the code of this website from here.
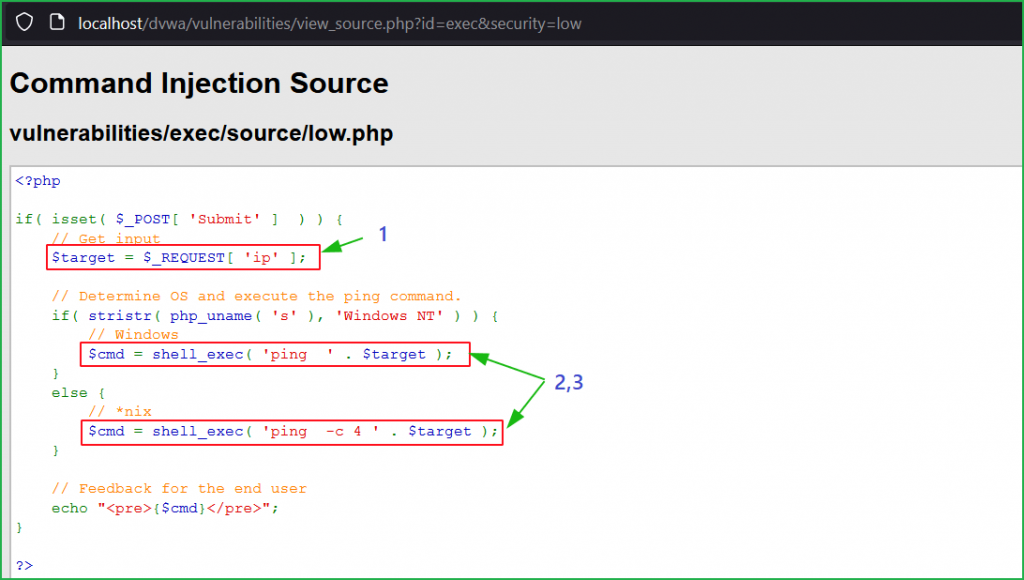
I made this website using Flask Framework and MySQL database. Command injection is a cyber attack that involves executing arbitrary commands on a host operating system (OS). Typically, the threat actor injects the commands by exploiting an application vulnerability, such as insufficient input validation. This form of cyberattack has been a persistent and evolving menace for decades, making it one of the most critical vulnerabilities in web applications.You can access the code of this website from here.
Read my latest thoughts on design, development, and trends from my github account. It contains all the notes of my learnings of new technologies and vulnerabilities. You can access my github account from here